The new database structures require new and powerful tools to manage databases in non-centralized solutions. The new data structures can be in large areas, and parts of them might be in different computers. This kind of network requires very good management. And fast reactions. In modern computing infrastructure networks play a vital role. When the system collects data from multiple sources, it should observe that data. That left from the source is the same in destiny.
In old times TCP/IP-protocol there system sent checksum or every data packet back to sender to compile that it's not changed is powerful. But when things like AI should collect data even from millions of sources, and then the system creates a new entirety. In that process, the TCP/IP is a too-slow protocol that can handle millions of bits that come from multiple sources. At the same time.
"A logo for SIEVE, created by Yazhuo Zhang, portrays hotter objects in shades of red and colder ones in shades of blue. Zhang also designed a web site for SIEVE, including a motion graphic demonstrating how it works. Credit: Yazhuo Zhang"
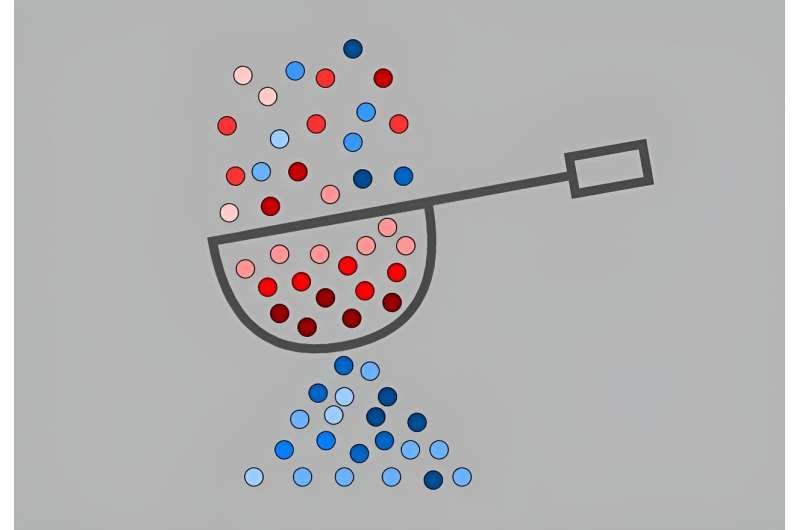
You can see how this new algorithm acts. The idea is that the system gets the command "select red balls". Then, the system just lets red balls through the filter or cache. The system keeps "red "or "hot" balls in place, where users can get them fast. The blue or "not so "popular" objects can let go somewhere where they don't fill the cache. So the system stores only "hot" data packs in the cache, and the system can put the rest of the data packs in hard disks.
The antivirus can also use this methodology. The antivirus can put its mark on data packages that it checked those data packages. The system can program those files that travel in it will not open until the antivirus checks them and puts the "pass" mark on those files.
************************************************************
"Cache-eviction algorithms determine what objects to toss and when to do so.
Computer scientists have developed a highly effective, yet incredibly simple, algorithm to decide which items to toss from a web cache to make room for new ones. Known as SIEVE, the new open-source algorithm holds the potential to transform the management of web traffic on a large scale.
FIFO, or “first-in, first-out,” is a classic eviction algorithm developed in the 1960s. Imagine objects lined up on a conveyor belt. Newly requested objects enter on the left and the oldest objects get evicted when they reach the end of the line on the right.
In the LRU, or “least recently used,” algorithm the objects also move along the line toward eviction at the end. However, if an object is requested again while it moves down the conveyor belt, it gets moved back to the head of the line.
Like LRU and some other algorithms, SIEVE makes a simple tweak to the basic FIFO scheme.
SIEVE initially labels a requested object as a “zero.” If the object is requested again as it moves down the belt, its status changes to “one.” When an object labeled “one” makes it to the end of the line it is automatically reset to “zero” and evicted.
A pointer, or “moving hand,” also scans the objects as they travel down the line. The pointer starts at the end of the line and then jumps to the head, moving in a continuous circle. Anytime the pointer hits an object labeled “zero,” the object is evicted.
'
The last part is from the ScitechDaily.com/ Revolutionizing Web Caching: Computer Scientists Unveil Simple Yet Game-Changing Algorithm
**************************************************************
Keeping ‘hot objects’ handy
Many people understand the value of regularly reorganizing their clothing closet. Items that are never used can be tossed and those that are rarely used can be moved to the attic or some other remote location. That leaves the items most commonly worn within easy reach so they can be found quickly, without rummaging around.
A cache is like a well-organized closet for computer data. The cache is filled with copies of the most popular objects requested by users, or “hot objects” in IT terminology. The cache maintains this small collection of hot objects separately from a computer network’s main database, which is like a vast warehouse filled with all the information that could be served by the system.
The last part is from the ScitechDaily.com/ Revolutionizing Web Caching: Computer Scientists Unveil Simple Yet Game-Changing Algorithm
********************************************************************
Separating "hot objects from data flow makes the system more effective. The system can transfer widely used data objects to another cache there is not so much data. Or it can transfer the most used data packages even to the workstation memories. Whenever a computer searches data that thing takes a couple of seconds. But what if there are billions of data packages stored in a cache, and the system always must search them by one to one? In large networks, there could be even thousands of queries all the time.
The SIEVE can also make networks faster because it helps to detect data packs that net protection programs like antivirus handle. The antivirus puts a mark on the data pack. And that mark allows programs to open the data pack. If there is no mark the data pack will transfer back to the antivirus.
If the antivirus doesn't check all things that travel in the network. That can cause malware infection. The antivirus can also put its mark on the data packs that it checked. That denies the ability to slip non-checked data inside the network.
The thing that makes this new algorithm effective is that it marks the data bite to value zero while it travels in line. And then SIEVE returns in value into one. when it's the end of the route. This thing helps things like antivirus programs separate data packages that are already analyzed. In this model, the "zero" means "don't touch". And the value one means that the system can catch the data pack.
https://scitechdaily.com/revolutionizing-web-caching-computer-scientists-unveil-simple-yet-game-changing-algorithm/
https://techxplore.com/news/2024-01-scientists-simple-method-cache-sifting.html